Date: 07-04-25
Introducing CoFHE: FHE-Based Encryption Everywhere With a Single Line of Code
The CoFHE testnet is now live on Ethereum Sepolia testnet, with additional EVM-compatible chains coming soon.
The Confidentiality Conundrum
While decentralization and transparency are key components of the crypto ethos, a completely and uncompromisingly translucent blockchain is not feasible for many of crypto’s most promising use cases. Whether it’s protecting user financial data, enabling private DeFi transactions, or securing sensitive enterprise operations, confidentiality is a critical piece currently missing in Ethereum as it stands today.
Until now, tools like zero-knowledge proofs (ZKPs), multi-party computation (MPC), and trusted execution environments (TEEs) have been used to enhance privacy. Each of these privacy enhancing technologies has its unique set of strengths and limitations. Unlike ZKPs, which only prove correctness without processing hidden data, or MPC/TEEs, which rely on trusted setups or hardware, FHE provides a decentralized way to execute private smart contracts while maintaining full composability with existing blockchain infrastructure.
Ethereum Virtual Machine (EVM) smart contracts currently operate in full uncompromising transparency—meaning every transaction, function call, and stored variable is visible onchain. While this transparency enables trustless execution, it also leads to several issues:
– Lack of financial privacy. DeFi users cannot shield their balances, trades, or lending activity.
– Enterprise data risks. Businesses cannot use public blockchains for sensitive operations without risking leaks.
– Front-running & MEV exploits. Traders face sandwich attacks, liquidations, and unfair pricing from visible mempool transactions.
– Compromised voting & auctions. Governance votes, sealed-bid auctions, and private agreements are difficult to implement securely.
Ethereum needs a solution to these problems if it is to reach the next level of adoption.
The Fix: An Interoperable and Performant FHE-Enabled Coprocessor
CoFHE leverages Fully Homomorphic Encryption (FHE) to enable confidential smart contracts on any EVM-compatible blockchain. This means data remains encrypted at all times, even during processing—enabling encrypted computation for anyone and everyone.
CoFHE enables real-time confidential compute, decryption at 50x faster than current competitor benchmarks, and seamless integration in smart contracts with a single Solidity import–all in a scalable architecture that ensures low gas costs, fast performance, and a clear path to verifiability.
CoFHE is like having the superpower of invisibility — always available when you need to keep things private, without compromising speed or usability
From the start, Fhenix’s mission has always been to bring FHE everywhere. That process starts with the builders. With CoFHE, we’re able to serve them up a steaming cup of confidentiality on demand wherever they are rather than asking them to come to us.
How CoFHE is Brewed
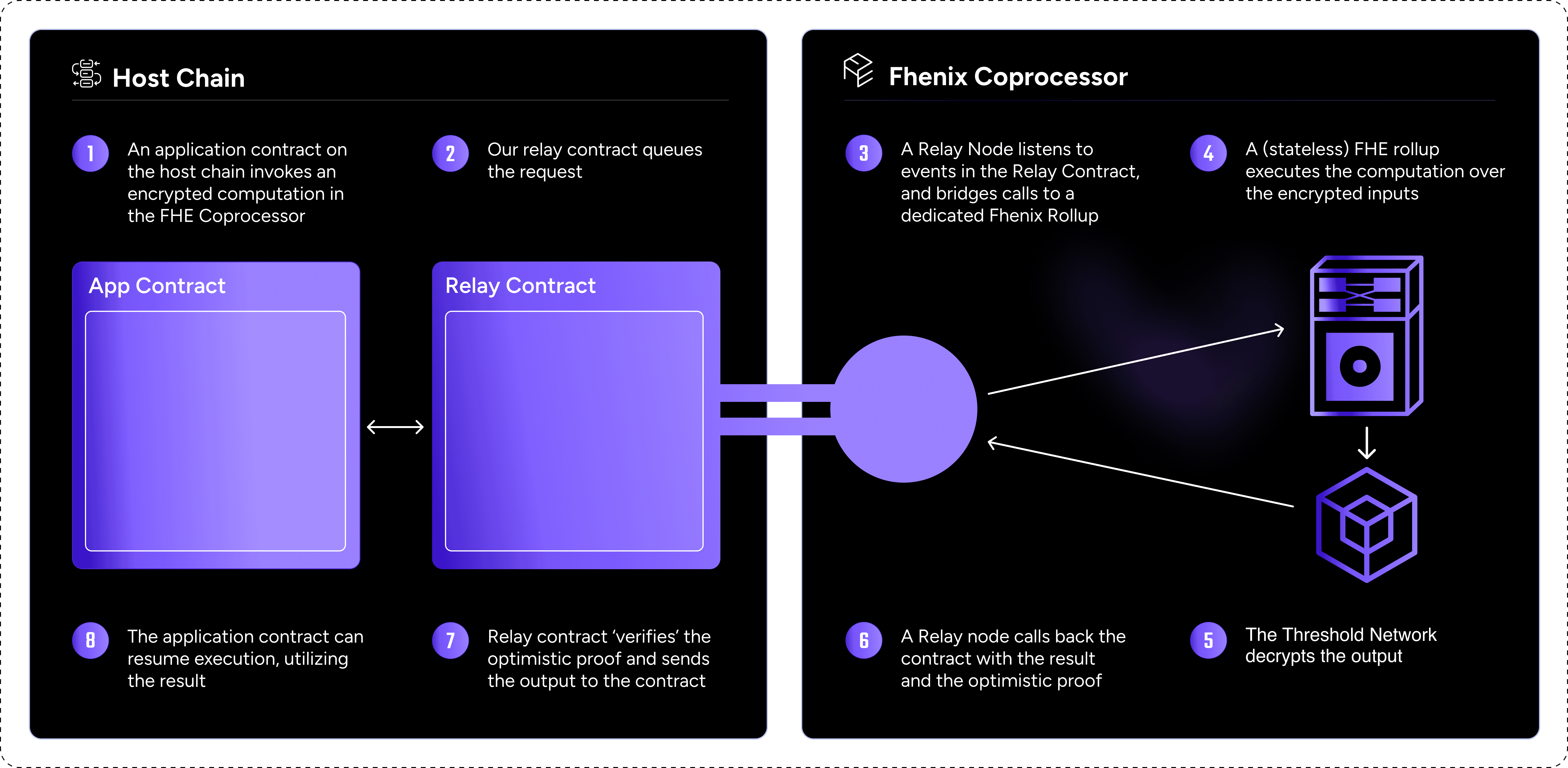
A simplified overview of how CoFHE works.
1. A smart contract makes an FHE operation request
2. The “Barista” contract emits an event saying, “Hey, there’s FHE work to do!”
3. Portafilter detects this event and routes the request to fheOS, the “brain” responsible for FHE processing
4. FHEOS processes the request, performs the encrypted computation, and sends the encrypted result back to the Portafilter
5. If the request is for decryption, the aggregator forwards it to the Fhenix Decryption Network, which securely decrypts the data
With CoFHE, gas fees are incurred on the chain where the smart contract is deployed, keeping the interactions straightforward.
In short: CoFHE delivers FHE-based confidentiality with a single line of code.
(For a more detailed and technical look at how CoFHE works, check out the developer docs).
One of the secrets to the CoFHE blend is the Fhenix Decryption Network (formerly called the Threshold Network), the system CoFHE uses to handle decryption. We’ll have more to share on the Decryption Network in an upcoming post, so stay tuned for that.
FHE Everywhere
Without confidentiality, mainstream users, enterprises, and institutions cannot fully embrace DeFi, DAOs, and other promising Web3 innovations. In order for any given privacy solution to stick, it must be seamless. CoFHE lowers the barrier of entry to FHE-based confidentiality, making it trivially easy for builders to tap into confidential compute.
We’re working closely with the OffchainLabs team on FHE research and development in order to bring FHE-based confidentiality to Arbitrum, Ethereum, and beyond.
Take a Sip
Builders, enterprises, and entrepreneurs can start building confidential applications using CoFHE today.
For integration guides and a more detailed look at CoFHE, see the developer documentation.
If you have any questions about CoFHE or FHE in general, ask away in the Fhenix Early Adopter Telegram channel.
CoFHE marks a new chapter for Ethereum and onchain confidentiality, one in which privacy is no longer an afterthought. With confidentiality and a little caffeine, anything is possible! ☕️✨